AWS WAF: A Practical Scenario and Solution
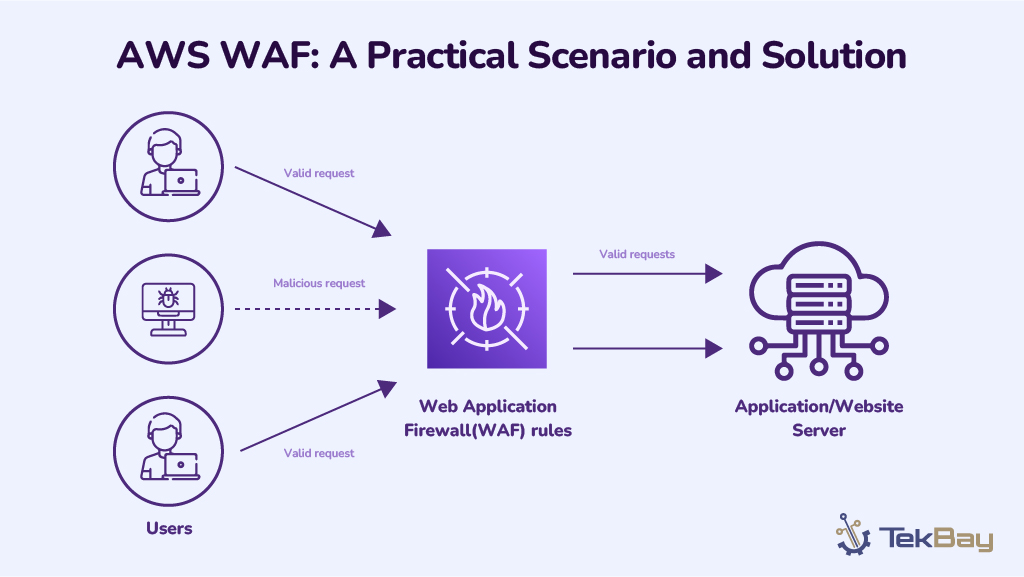
While the shift to cloud infrastructure offers organizations benefits like flexibility and cost efficiency, securing applications requires more than simply migrating to the cloud. To stay ahead of evolving cyber threats, you need an innovative yet robust approach, and the AWS WAF (Web Application Firewall) is your go-to option. Designed to address modern security challenges, the AWS […]
Layer 2 Attacks and Mitigation Techniques: DHCP Snooping for Network Protection
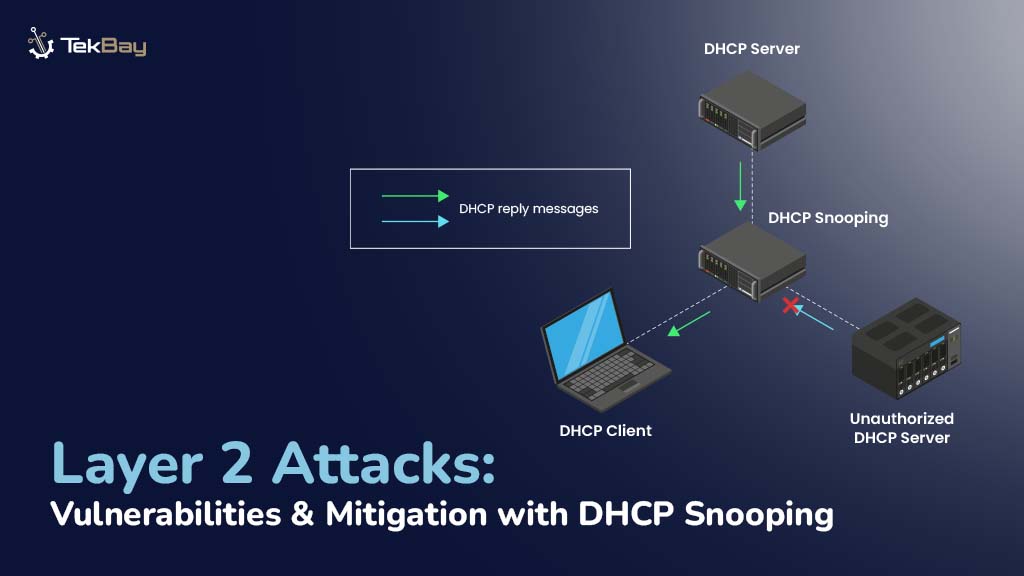
Layer 2 attacks, which target the OSI model’s data connection layer, pose significant dangers to local area networks (LANs). Attackers frequently target this layer to exploit inherent vulnerabilities, most of which are associated with DHCP (Dynamic Host Configuration Protocol). Whether it’s a DHCP starvation attack flooding your IP pool with bogus requests or a rogue […]
Exploring AWS Resilience Hub Capabilities

Resilience is the capability of any system to bounce back from unexpected problems like hardware failures or natural disasters. Obtaining resiliency is all about minimizing downtime, protecting your data, and ensuring your services keep running smoothly, no matter what type of problems happen. Backing up your resources, using auto-scaling mechanisms, setting up required alarms, and […]