Explore The TekBay Journal
A collection of stories about our people, our expertise, our innovations and the evolving journey of our firm.
Empowering Businesses with Amazon Textract: Comprehensive Guide
The ability to quickly extract valuable insights from documents is crucial. However, managing and processing unstructured data from various formats,…
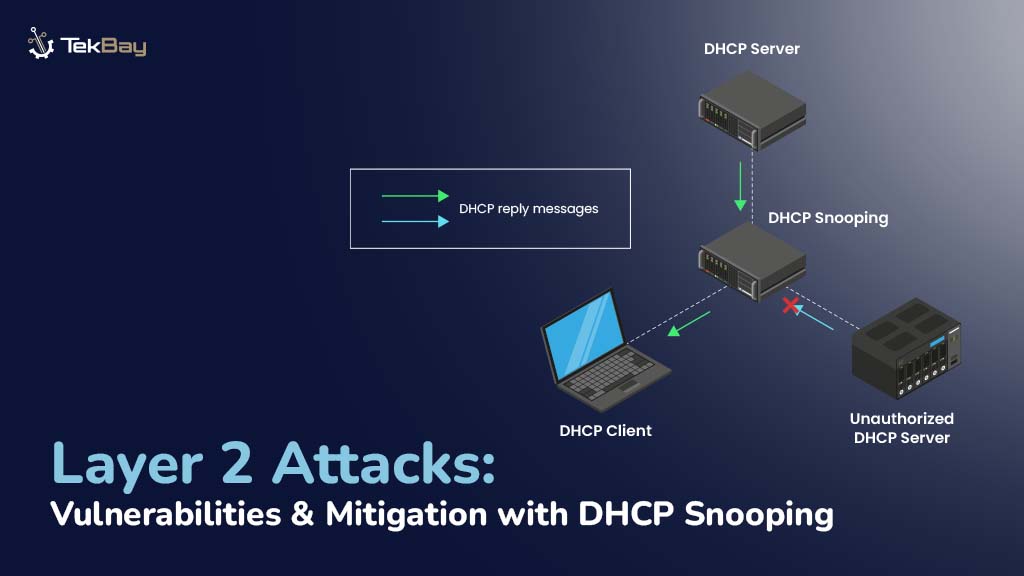
Layer 2 Attacks and Mitigation Techniques: DHCP Snooping for Network Protection
Layer 2 attacks, which target the OSI model’s data connection layer, pose significant dangers to local area networks (LANs). Attackers…
Exploring AWS Resilience Hub Capabilities
Resilience is the capability of any system to bounce back from unexpected problems like hardware failures or natural disasters. Obtaining…
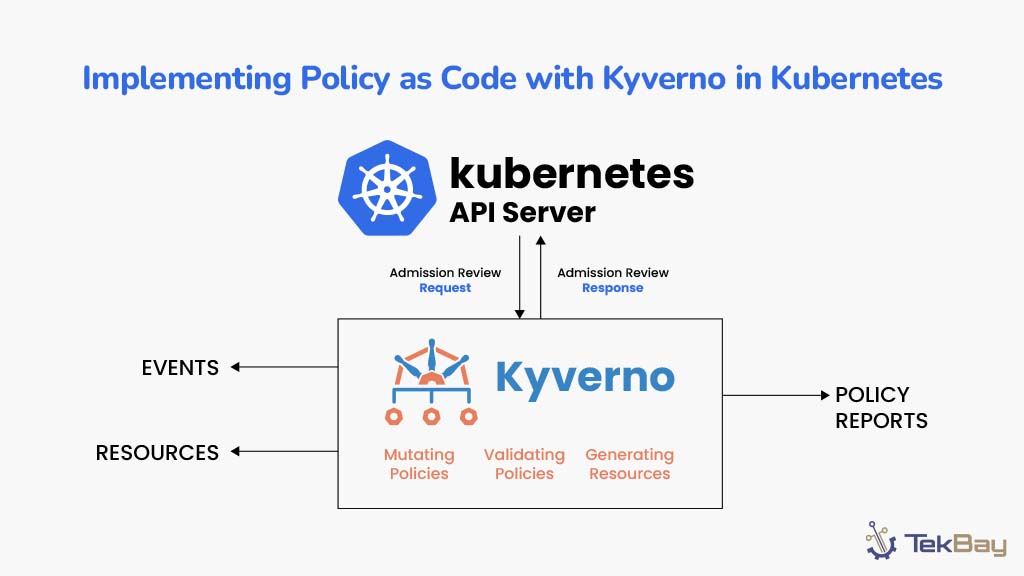
Achieving Policy as Code with Kyverno in Kubernetes
Kubernetes environments thrive on flexibility and scalability, but these benefits also present challenges in maintaining consistency in governance, security, and compliance. …
Deploy DeepSeek-R1 LLM Locally with Ollama and Open WebUI
Large Language Models (LLMs) are transforming AI development, but running them locally can be challenging without the right tools. Available…
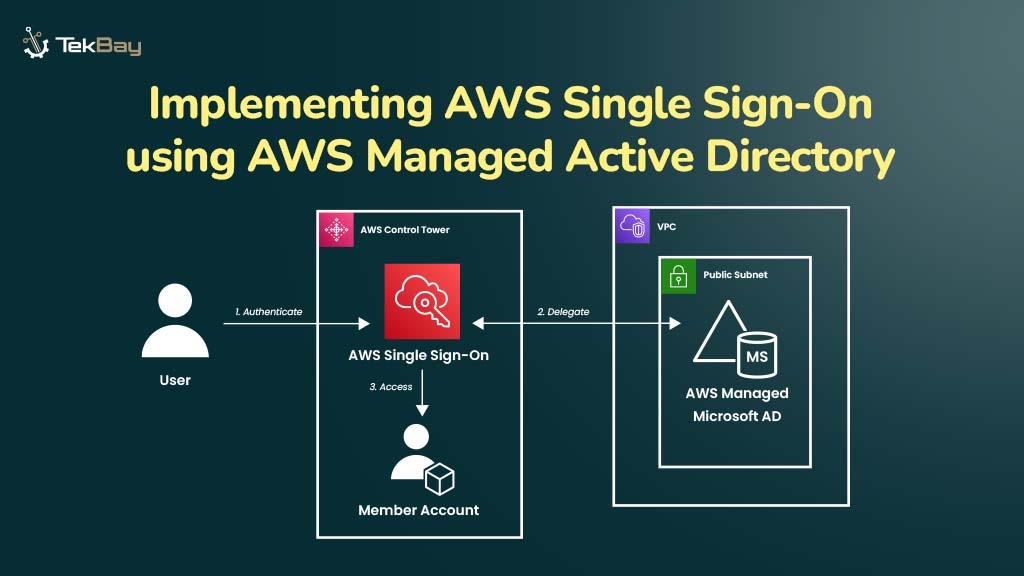
Implementing AWS Single Sign-On (SSO) Using AWS Managed Microsoft AD
AWS Single Sign-On (SSO), now known as IAM Identity Center, allows users to access both AWS and on-premises resources with…
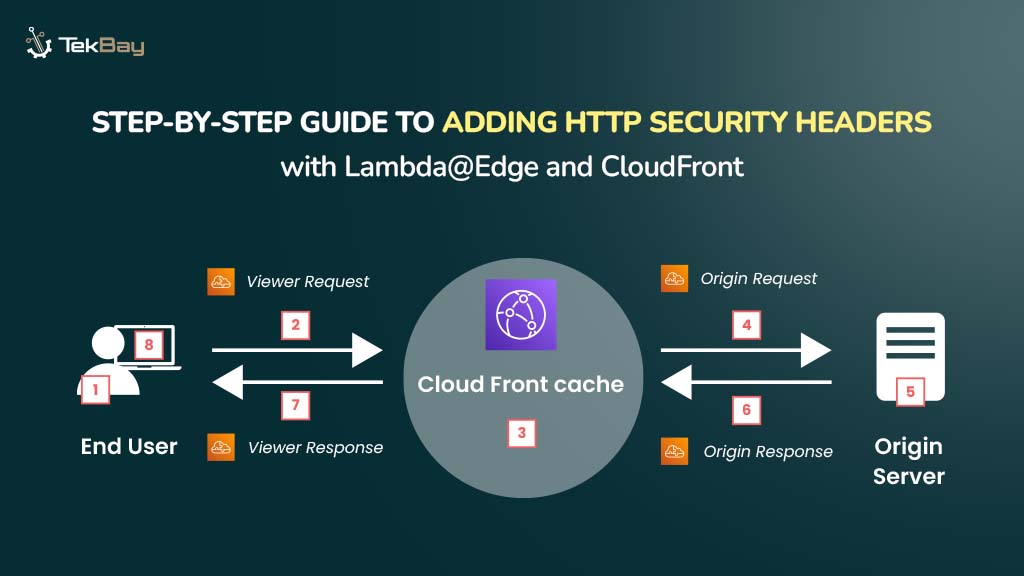
How to Add HTTP Security Headers with Lambda@Edge and CloudFront
Web security has become more crucial than ever! HTTP Security Headers are your first line of defense to safeguard your website—or any…
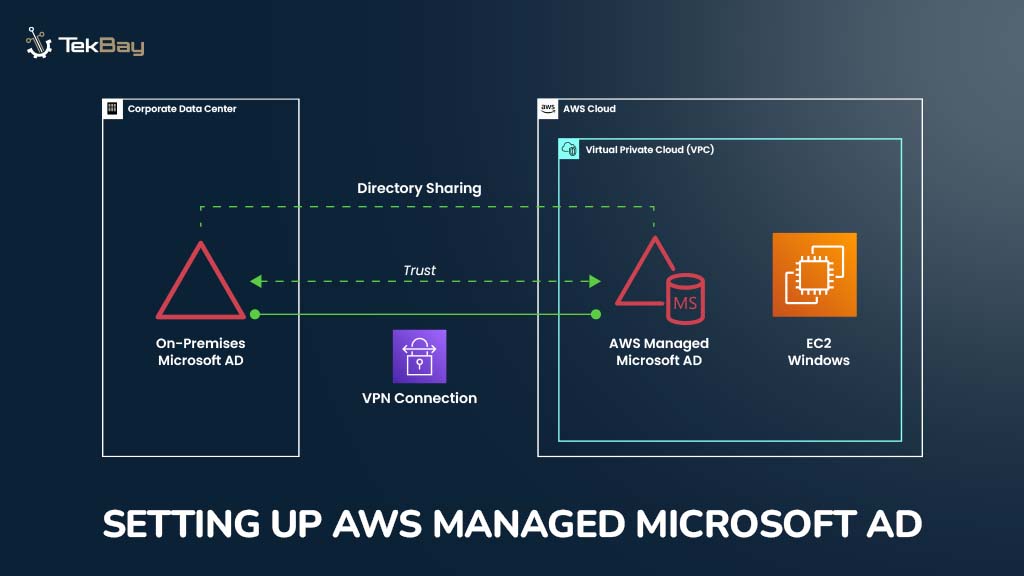
Setting up AWS Managed Microsoft AD: Step-By-Step Guide
In Part 1 of our three-part blog series, “Connecting Your On-Premises Network to AWS,” we established a secure connection between the on-premises network…
How to Submit an AWS Consent to Assignment Request
When transferring an AWS account between two legally distinct entities, such as during a merger, acquisition, or divestiture, AWS requires…